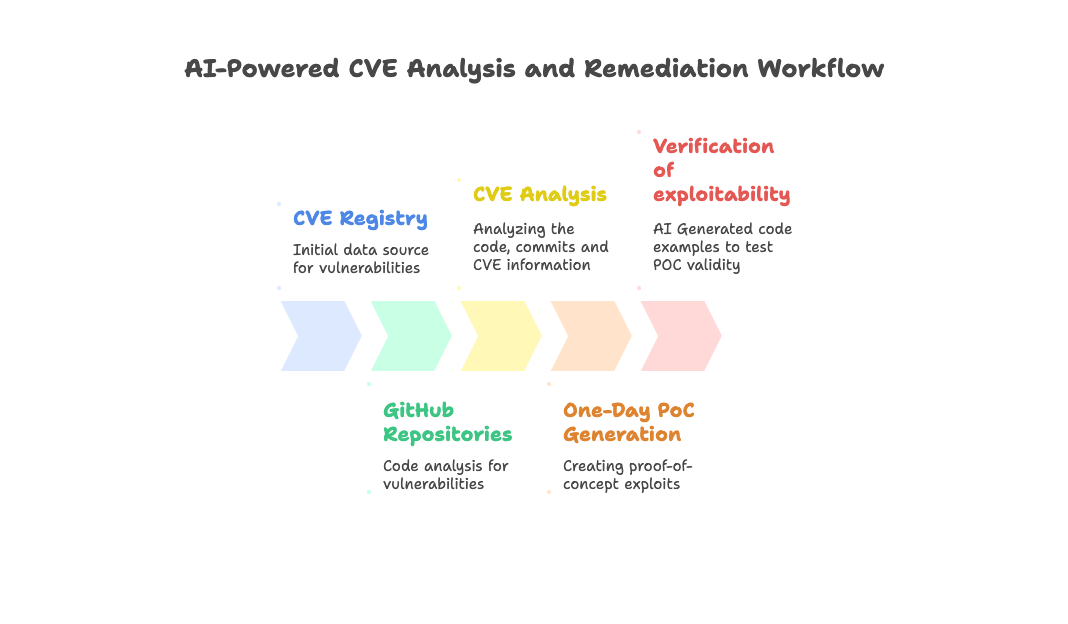
Password + authenticator vs passwordless
Going through Entra ID training modules. It has phone sign-in, windows hello, FIDO2 security key, and certificates as more secure. Can someone explain why that is? 2FA has been the standard for years. I'm aware sms can be compromised, is this now the case for authenticator apps as a whole as well? What makes the above listed different? submitted by /u/PaulTheMerc [link] [comments]